May 31, 2023 CISA KEV Breakdown | Barracuda, Zyxel

May 31 (and May 26): 2 New Vulns | CVE-2023-28771, CVE-2023-2868
In this CISA KEV Breakdown, two command injection vulnerabilities from Zyxel and Barracuda Networks were added. CVE-2023-2868, the vulnerability found in the Email Gateway Service of Barracuda, was patched as a 0-day on May 20, with another follow-up patch May 21. In Barracuda’s report, they indicate earliest observed exploitation of the vulnerability to be October of 2022.
Shadowserver has observed mass scanning activity across over 700 IKEv2 sensors for CVE-2023-28771, to which they infer that still-vulnerable devices should be assumed compromised. Organizations can detect indicators via the log message written to /tmp/sdwan_vpndebug.log with the content vpn_info: [cgnat] 4th cgnat convert wrong. It is important to note that this log entry existing does not immediately indicate exploitation has occurred, it more so indicates that a packet was processed that reached the vulnerable code path. If this is identified in your environment, correlation of surrounding activity to the affected host and from the sender of the packet should better indicate actual compromise.
Notable Vulnerability Additions
CVE-2023-28771 | Zyxel Multiple Products Command Injection
A vulnerability affecting Zyxel ATP, USG, FLEX, VPN and ZyWALL/USG can allow an attacker to remotely execute arbitrary code. The vulnerability exists due to the fact that a decoding function mixed with an insecure logging function allows an attacker to send an IKEv2 Notify payload with an injected command provided in the Notification Data field if the message-type is NO_PROPOSAL_CHOSEN. The decode function intakes an incoming payload of this type, and the data is written by the logging function to a file directly using the system command.
The following software versions are reported as affected:
- ATP (Firmware version 4.60 to 5.35 inclusive)
- USG FLEX (Firmware version 4.60 to 5.35 inclusive)
- VPN (Firmware version 4.60 to 5.35 inclusive)
- ZyWALL/USG (Firmware version 4.60 to 4.73 inclusive)
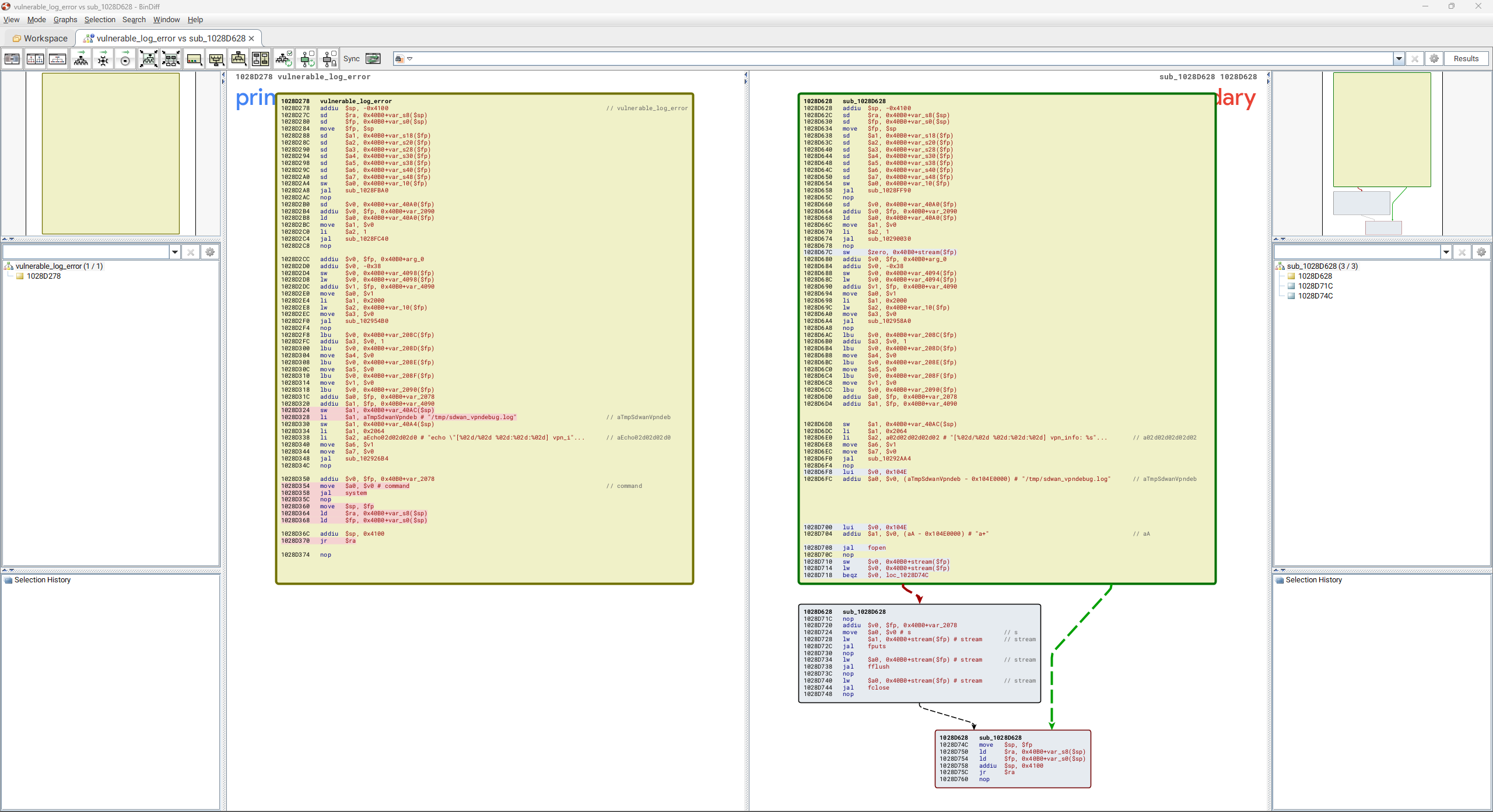
Below is an image from Rapid7’s report on the vulnerability posted to AttackerKB. Reversing the firmware updates show the removal of the use of system to write to the file (left box), with the replacement being a set of calls via fopen, fputs, fflush and fclose (right box). This is a more secure method for writing directly to the log file, as it avoids using a command that invokes a shell. Be sure to check out Rapid7’s report to better understand the discovery and PoC that exploits the vulnerability.
Security Advisory(s):
CVE-2023-2868 | Barracuda Email Security Gateway Command Injection
A vulnerability affecting Barracuda Email Security Gateway versions 5.1.3.001-9.2.0.006 allows for an attacker to achieve code execution via command injection. The vulnerability exists due to incomplete validation of user-supplied .tar filenames. An attacker can format file names in a particular manner that would result in remotely executing a system command through Perl’s qx operator with the privileges of the Email Security Gateway product. Exploit code does not appear to be publicly available at this time.
Barracuda has indicated as of May 30 in their ongoing report that confirmed exploitation was used to deploy malware. To see more detail surrounding observed malware and IoCs, see their advisory below. Mandiant was initiated to work alongside Barracuda in their response efforts. So far, Mandiant has associated this activity with UNC4841, a suspected espionage threat actor that leveraged the 0-day in a range of public and private sector attacks. Keep up to date with Barracuda’s response via their status page as well.
Security Advisory(s):
https://www.barracuda.com/company/legal/esg-vulnerability
← May 22, 2023 CISA Kev Breakdown
Click here to expand our CISA KEV Breakdown Frequently Asked Questions
- What makes for a notable addition?
- A notable addition can arise from many different characteristics. If a particular vulnerability is notable to the security community or a subset of the security community or if the EPSS score reveals notable information about the vulnerability, this can constitute further analysis. It may also be the case that a particular vulnerability shines a light on everyday users and we will highlight important information and key takeaways to ensure users and readers have easy access to actionable information.
- When is the Breakdown released?
- We aim to have our analysis of each KEV update posted within 24 hours of the time in which the Catalog is updated. See CISA’s full catalog here
- I am not bound by BOD 22-01 or federal regulations, why should the KEV concern me?
- CISA encourages all organizations to utilize the Catalog as an attribute in your vulnerability prioritization framework. Organizations looking to lessen the scope on known dangerous vulnerabilities and make a goal to remediate them can understand where they currently stand against what CISA has confirmed as exploited vulnerabilities in the wild. See CISA’s section on “How should organizations use the KEV catalog?” here.
- What is EPSS?
- EPSS is the Exploit Prediction Scoring System. It is an open, data-driven effort for estimating the likelihood (probability) that a software vulnerability will be exploited in the wild. See the EPSS home page on FIRST for more information here.
- What is the difference between EPSS probability and EPSS percent?
- EPSS probability is the risk calculated by the model when determining the perceived threat of the vulnerability itself. Percentage is a relative comparison of the rest of the CVEs within the given sample. While the probability only changes upon refreshing the results from the model, the percentage can change purely based on the CVE sample given. In the case of the Breakdown, we use the percentage given by the pool of all CVEs with given EPSS data. Scores may vary post-release of the post given new information about the vulnerabilities and their perceived threat. For more information on applying and understanding EPSS data, see this article on the FIRST website, as well as their FAQ page.
- What is GreyNoise?
- GreyNoise is a platform that collects, analyzes, and labels data on IPs that scan the internet and saturate security tools with noise. Through their sensor network, GreyNoise observes vulnerability exploitation attempts for vulnerabilities that are exploited in the wild over the Internet. These are arguably vulnerabilities that should be at the very top of your priority list to remediate.
- Why are GreyNoise exploitation attempts only observed on ~20% of KEV vulnerabilities?
- Exploitation of many vulnerabilities in the CISA KEV will not be observed for many reasons that GreyNoise does a good job of explaining in this post. For example:
- The vulnerability may not be remotely exploitable
- Vulnerability exploitation may require authentication (and result in privilege escalation)
- The impacted software may not be exposed to the internet
- Mass scanning/exploitation is not occurring yet
- Exploitation of many vulnerabilities in the CISA KEV will not be observed for many reasons that GreyNoise does a good job of explaining in this post. For example:
See Nucleus in Action
Discover how unified, risk-based automation can transform your vulnerability management.