What is OWASP ZAP?
An introduction to OWASP ZAP and instructions on how to get ZAP asset and vulnerability data into Nucleus.

ZAP is an open-source tool for web application scanning and pen testing maintained by OWASP. According to the OWASP ZAP website, it is the world’s most popular free web security tool.
How does OWASP ZAP work?
ZAP sits between a web app and the pen tester’s client. In this way it becomes a proxy for capturing the data being transmitted and determining how the application will respond to potentially malicious requests. ZAP is designed to be flexible and accessible to a variety of security professionals at varying skill levels and job roles. Additionally, because of its open-source nature, anyone can check out the source code and contribute to it.
Who is OWASP?
OWASP (Open Web Application Security Project) is a nonprofit foundation and primarily an online community of security professionals concerned with improving software security. It publishes resources for web application security best practices and is a highly regarded organization. The Nucleus co-founders, all security professionals themselves before launching Nucleus, are big fans of OWASP .
Why is ZAP Important?
ZAP is a free open source (DAST) tool that allows security testers to effectively detect common threats to web applications. These threats include common ones like:
- SQL injection
- XSS (Cross-site scripting)
- CSRF (Cross-site request forgery)
- Misconfigurations
- Data leakage
You can learn more about the most common threats to web applications in the well-traveled OWASP Top Ten Web Application Security Risks.
Also important, is that the tool is easy to use for most users and available on all major operating systems. It’s also maintained by a community of contributors who are passionate and dedicated.
Does Nucleus integrate OWASP ZAP?
Yes, Nucleus supports API push calls and manual scan file uploads from OWASP ZAP.
Getting ZAP Data into Nucleus – 3 Simple Steps
Importing and viewing scan data from OWASP ZAP into Nucleus is fast and is achieved in just three simple steps.
Step one is generating a ZAP report. This can be done from the ZAP UI, command line, or by using the API to push to Nucleus. Step by step instructions for how to do any three of these operations can be found here in the ZAP documentation.
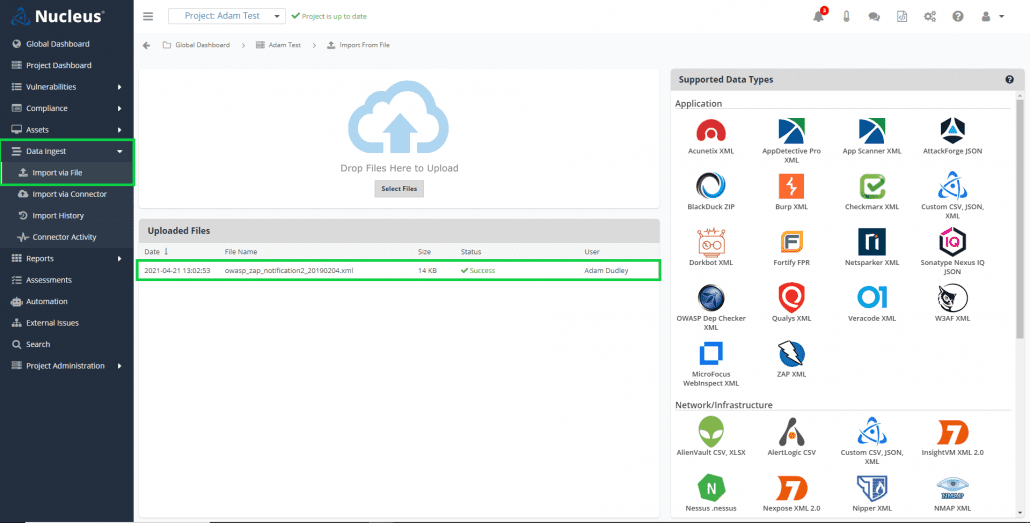
Step two, unless you have used the ZAP API to push your report directly to Nucleus, is to import the exported report file to your Nucleus instance. To do this, from within a Nucleus project, navigate to Data Ingest > Import via File. From the Import via File page, either drag and drop your ZAP file or select it from your file system. Your file will be imported immediately provided you do not have other files ahead of the ZAP file in your job queue.
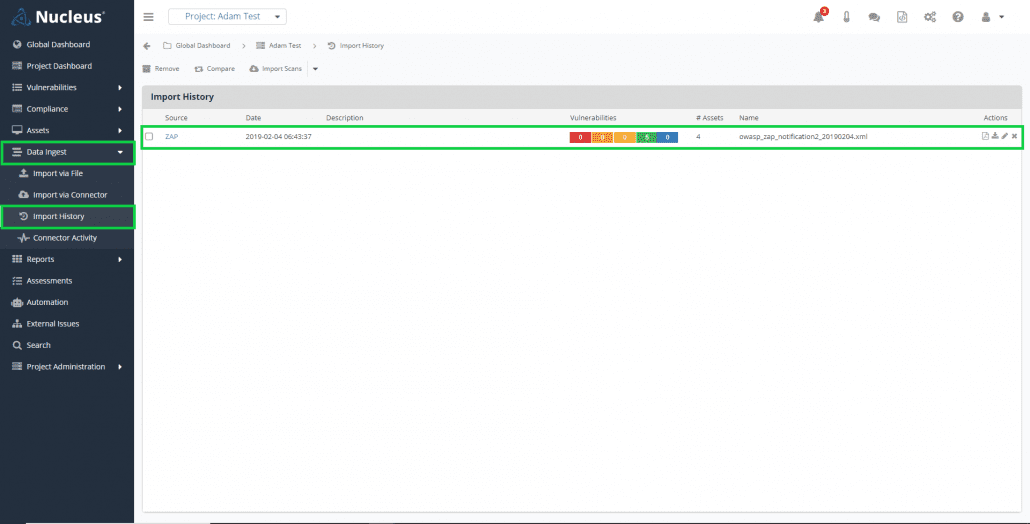
Step three, once you have received a successful file ingest message, is to view your data. From within a Nucleus project, navigate to Data Ingest > Import History. Find the scan import in the Uploaded Files section and click the File Name.
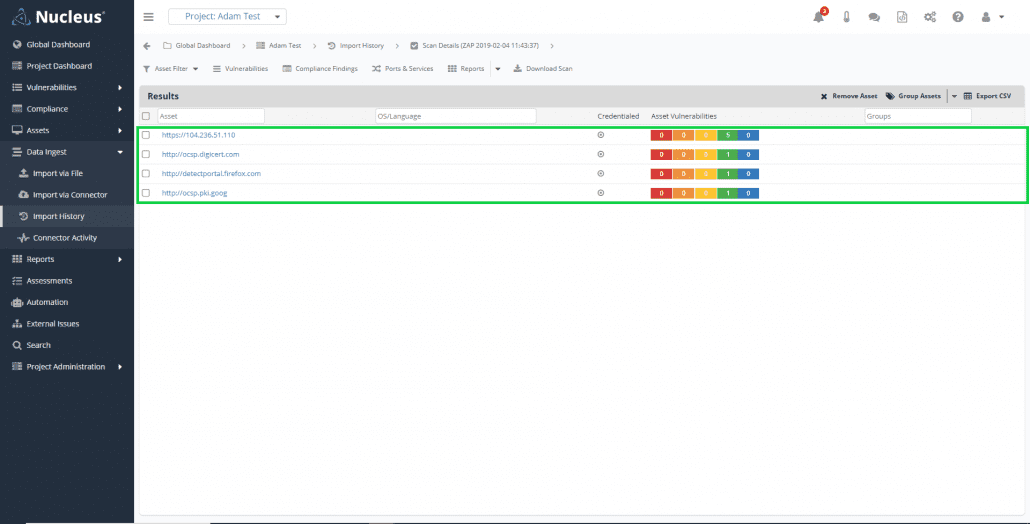
In this import details view, you’ll be able to see any assets and vulnerabilities that Nucleus discovered in the ZAP scan. By clicking on the asset name, you can then drill down to the asset view to see its metadata, edit its details, and/or take a closer look at the vulnerabilities.
OWASP ZAP is a powerful open-source tool for identifying security vulnerabilities in web applications. With Nucleus, it’s fast to get your ZAP data ingested so you can see it alongside data coming in from other scanning tools you have connected to Nucleus. To see all 70+ scanning and other types of security and workflow tools Nucleus supports and integrates with, visit our Supported Integrations page.
See Nucleus in Action
Discover how unified, risk-based automation can transform your vulnerability management.