Nucleus Release 2021-04-08
We’re pleased to bring you yet another new release of Nucleus with enhancements and new integrations! Take a look at some of the highlights.

.
Yet another release packed full of updates. See below to find out more!
Amazon Web Services Connector
At Nucleus, one of our guiding principles is to listen to our customers and build functionality that makes the vulnerability management lifecycle as quick and painless as possible so that more time can be spent on high-value tasks.
True to this principle, we’ve previously released two powerful connectors that integrate with Amazon Web Services (AWS), providing customers with vulnerability data identified by AWS Inspector, as well as synchronization with AWS EC2 instances so that you can keep on top of what your attack surface actually looks like. Since then we’ve been listening to your feedback on how you use these connectors so that we can make them even better than they already are.
Today we’re excited to announce a brand new connector called the Amazon Web Services connector which integrates our two previous connectors into a single authentication flow and will serve as the foundation for scaling out support for more AWS services in the future cough ECR is next cough cough. This connector is the latest step in our push towards making the ingestion of cloud asset and vulnerability data a quick and painless task.
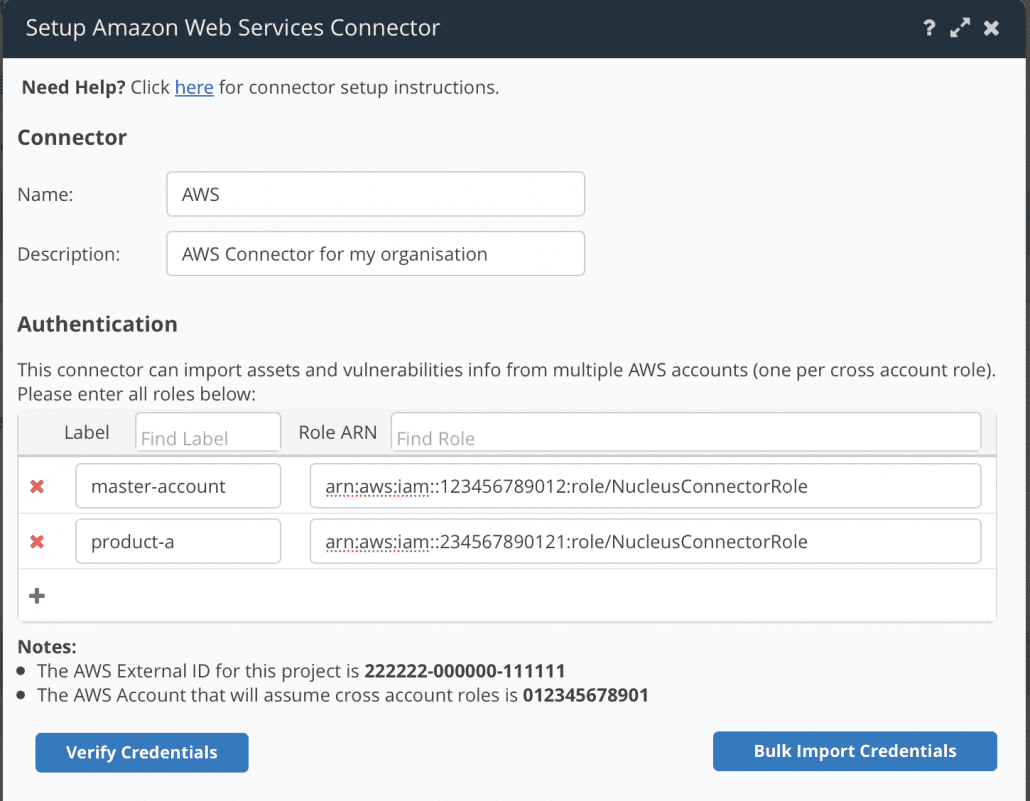
With this release, the AWS connector becomes a single place for you to set up and manage access to all of your AWS accounts in your Nucleus project by leveraging cross-account IAM roles. IAM roles can be created directly in the AWS Console, or deployed using CloudFormation which we’ve provided a handy CloudFormation template for.
Once roles are deployed to your AWS accounts, you can then add role ARN’s directly in the connector setup page and Nucleus handles the rest! For more information on setting up the new AWS connector as well as the CloudFormation template, see our help documentation here.
This connector also brings with it a number of enhancements to both our AWS Inspector and EC2 integrations.
AWS EC2
You can now manage a single Asset Inventory Sync rule for all of your AWS accounts across all regions in your Nucleus project. Simply go to the Asset Inventory Sync tab of the Automation page and click Add Rule. Select your AWS connector, the regions, and accounts that you want to synchronize instances from, and hit Save & Finish.
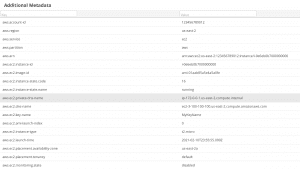
The synchronization rule now also ingests all available metadata as Additional Metadata which can be viewed under the Asset Details page, as well as leveraged to construct powerful rules in the Nucleus Automation Engine:
AWS Inspector
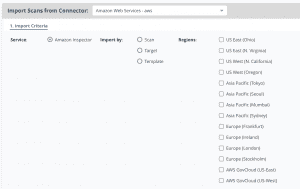
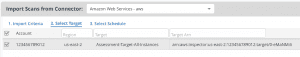
The AWS Inspector integration has been turbocharged with new functionality and flexibility. You can now import vulnerability results by Scan, Target, or Template, as well as select the regions that you want to query and ingest data from:
Once you’ve chosen the import method and regions, you’re then presented with all available results across each account that you’ve set up in the connector, and can further filter by region and other information:
Please note that with this release we’ve deprecated the existing EC2 and Inspector connectors, as well as authentication via IAM access keys. They will be continued to be supported for existing customers during the transition period, but no new features will be released for the previous AWS EC2 or Inspector connectors.
Vulnerability Triggers in Automation Rules
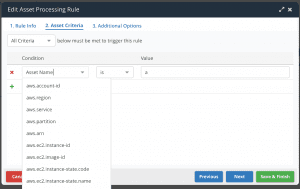
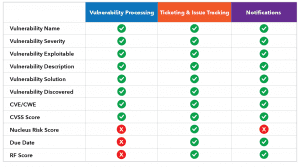
We’ve been working hard behind the scenes to make the Nucleus Automation Engine even better than it already is. In this release we’ve updated the Vulnerability Processing, Ticketing & Issue Tracking, and Notifications rules so that they can be triggered based on more vulnerability conditions:
Complete list of changes and bug fixes…
- NEW There is a new Amazon Web Services connector that unifies EC2 and Inspector.
- NEW Authentication to AWS services is via cross-account roles.
- NEW You can now sync AWS EC2 assets from multiple regions and accounts using one rule.
- NEW You can now ingest AWS Inspector results by Scan, Target or Template.
- NEW You can now ingest AWS Inspector results from multiple regions and accounts in one place.
- UPDATE Additional Metadata is now populated for AWS EC2 instances.
- UPDATE Vulnerability triggers for applicable Automation rules have been expanded with more conditions.
- BUG FIX Fixes to the clarity of error messages.
- BUG FIX Fixed an issue concerning the ServiceNow Company field.
- BUG FIX Fixed an issue in the Vulnerability Details Excel report where asset filters were not applied in certain situations.
- BUG FIX Fixed an issue where the Microsoft Defender machine Id was not available as asset criteria in automation rules.
- BUG FIX Fixed an issue where the trends page would not correctly filter the date range in certain situations.
- BUG FIX Fixed an issue where the Qualys connector would only import the first 1000 tags.
- BUG FIX Fixed an issue where intermediary and root certificates were shown on the Certificates Summary page.
- BUG FIX Fixed an issue where open ports were imported twice from the Qualys connector in certain situations.
- BUG FIX Fixed an issue where the last seen filter on the Active Vulnerabilities page was not including vulnerabilities from the same day.
- BUG FIX Fixed an issue where the Microsoft Defender connector would timeout for extremely large scans.
- BUG FIX Fixed an issue where the PCI Executive Report would show an incorrect finding compliance status.
See Nucleus in Action
Discover how unified, risk-based automation can transform your vulnerability management.