Nucleus Release 2021-3-24
We’re pleased to bring you yet another new release of Nucleus with enhancements and new integrations! Take a look at some of the highlights.

.
As you can see, we’ve been busy here at Nucleus! Another release packed full of updates. See below to find out more!
Vulnerability Due Dates
As organizations mature their vulnerability management programs, it has become increasingly common (and necessary) to set and track Service Level Agreements (SLAs) for how and when a vulnerability is treated. This can be particularly helpful in large organizations, where security policies define expected remediation effort and timelines for different classes of vulnerabilities in different situations.
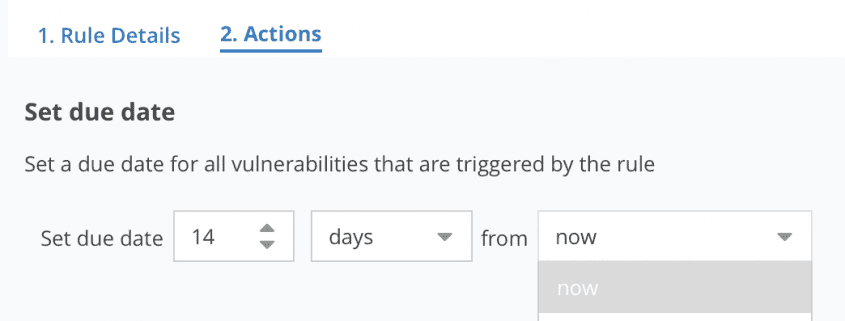
In this release we’re introducing our first foray into SLAs, Vulnerability Due Dates. Vulnerability Due Dates allow you to set when remediation efforts on vulnerabilities must be completed by, and track and report on vulnerabilities that are approaching their due date or have exceeded that date.
Using the Nucleus Automation Engine, you can create vulnerability processing rules which, based on all of the available vulnerability and asset criteria, enable you to automatically set due dates for vulnerabilities. Rules can be configured to set the due date as a set number of days, weeks or months from the time of ingestion, or the vulnerability’s discovered date.
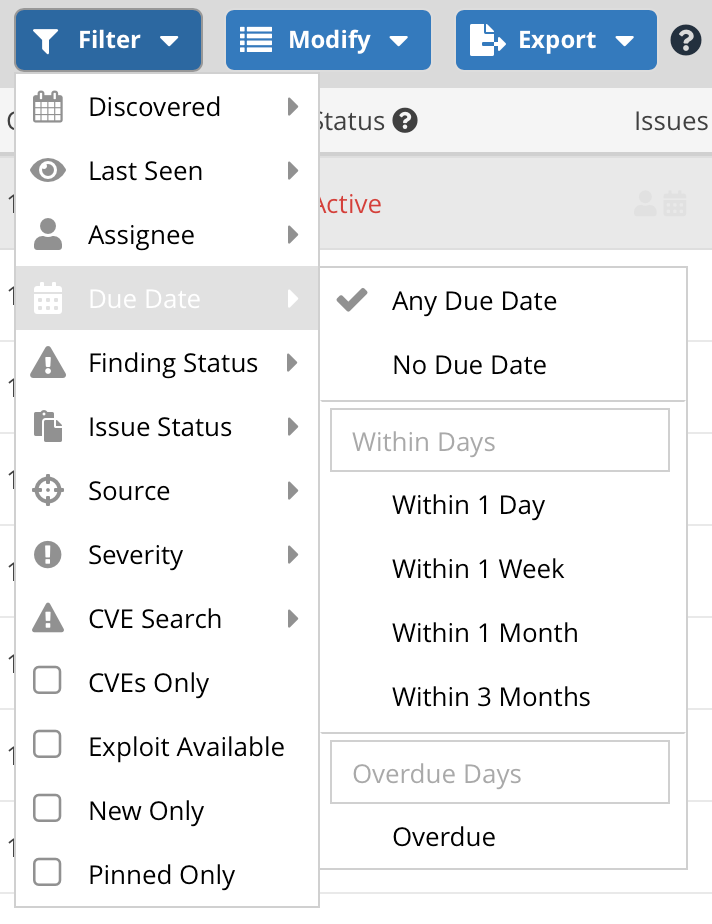
Once set, you can identify and measure vulnerabilities in the Active Vulnerabilities page by due date, including whether a due date is not set, when a vulnerability is due within days, weeks or months, and when vulnerabilities are overdue!
Assetnote
This release we’re excited to announce a new connector with Assetnote! Assetnote is an Attack Surface Management platform that identifies an organizations external facing systems and continuously monitors those systems for exploitable vulnerabilities.
We’ve worked closely with the team at Assetnote to create a connector that integrates with the Assetnote Notification Pipeline so that when assets and vulnerabilities are discovered across your environment, they surface in to your Nucleus project(s) in real time. When combined with the Nucleus Automation engine, you can create powerful and intelligent rules to suit your specific use case.
Read about setting up the Assetnote connector here.
Quick Filters for Active Vulnerabilities
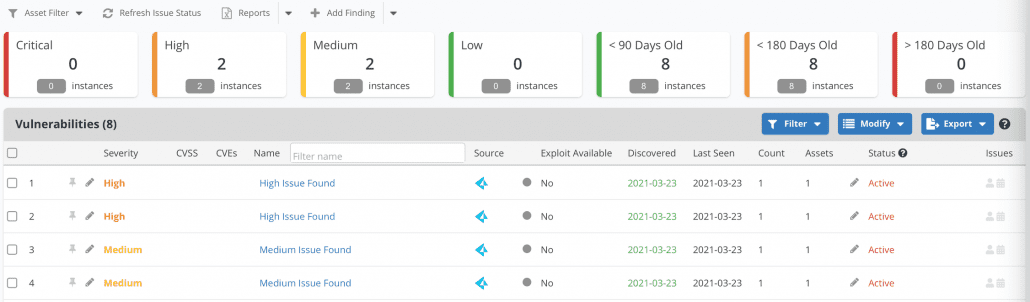
The Active Vulnerabilities page has received a face lift to ensure that you are able to identify and track the vulnerabilities that matter to you most. We’ve introduced an updated Quick Filter pane at the top of the page that shows you the numbers of vulnerabilities. In one click you can drill down to the vulnerabilities that are most important to you.
We’ve also updated the Source column with vulnerability source tool icons to make it easier for you to quickly identify where a vulnerability came from.
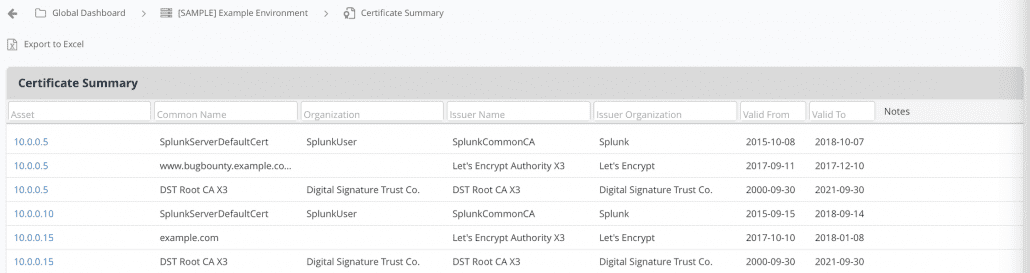
Asset Certificate Summary
We added a Certificate Summary view to the Assets menu to make it easy to view and report on certificates. This view includes all the usual filters for quick drilldowns. Plus, you can export to a downloadable report in one click.
Complete list of changes and bug fixes
- NEW You can now set when a vulnerability is due by Automation rules and manually in the UI.
- NEW There is a new Assetnote connector.
- NEW There is now an asset certificate summary page to view all certificates on all identified hosts.
- UPDATE The Active Vulnerabilities page’s top pane has been updated with improved quick filters, showing unique and all instances of vulnerabilities.
- UPDATE The vulnerability details excel report now includes an exploitable column.
- UPDATE The Qualys connector now ingests all exploitability information into the vulnerability description.
- UPDATE Source code repository branches and container image repository tags no longer count towards individual asset counts. I.e., one application license is consumed for one source code repository and one container image repository.
- UPDATE Vulnerability source tools now use icons.
- UPDATE There have been speed improvements to calculating and displaying vulnerability analytics.
- BUG FIX In certain circumstances scan imports from Prisma Cloud were not matching vulnerabilities correctly.
- BUG FIX Group imports from Qualys now work even if there is no WAS account access.
- BUG FIX There was an issue with OWASP scan imports creating too many findings for non-vulnerable informational findings.
- BUG FIX There was an issue with importing the same asset multiple times from Microsoft Defender for Endpoint.
- BUG FIX There was an issue with calls to Microsoft Defender for Endpoint timing out in certain situations.
- BUG FIX Occasionally Nested Asset groups were not showing correctly when assets were ingested from Qualys.
- BUG FIX In certain situations asset decom rules were not applying to assets with Assessments.
- BUG FIX Nested asset groups that didn’t exist when setting an asset processing rule weren’t nesting.
- BUG FIX There was an issue with scans within zip files not always ingesting correctly.
See Nucleus in Action
Discover how unified, risk-based automation can transform your vulnerability management.