Nucleus Release 2021-04-29
We’re pleased to bring you yet another new release of Nucleus with enhancements and new features! Take a look at some of the highlights.

.
Let’s paint a picture. It’s a bright sunny day in Florida and the Nucleus Ninja is out walking his Ninja-dog, Ninken, next to the local alligator pond. This gives the Nucleus Ninja a chance to clear his head and think about our customers, and that’s when it hits him, the dawning realization that may just be the answer to “how to do automation in the context of vulnerability management”.

This release is all about how to start doing automation of vulnerability management at scale. We announced our push towards better automation in our first Quarterly Customer Webinar, and this release is all around going down that path. We’ve designed a brand new workflow, introduced a templating language, and updated a lot of areas to make Nucleus just that much better around automating workflows. And without further ado, here’s what we’ve been up to the past month…
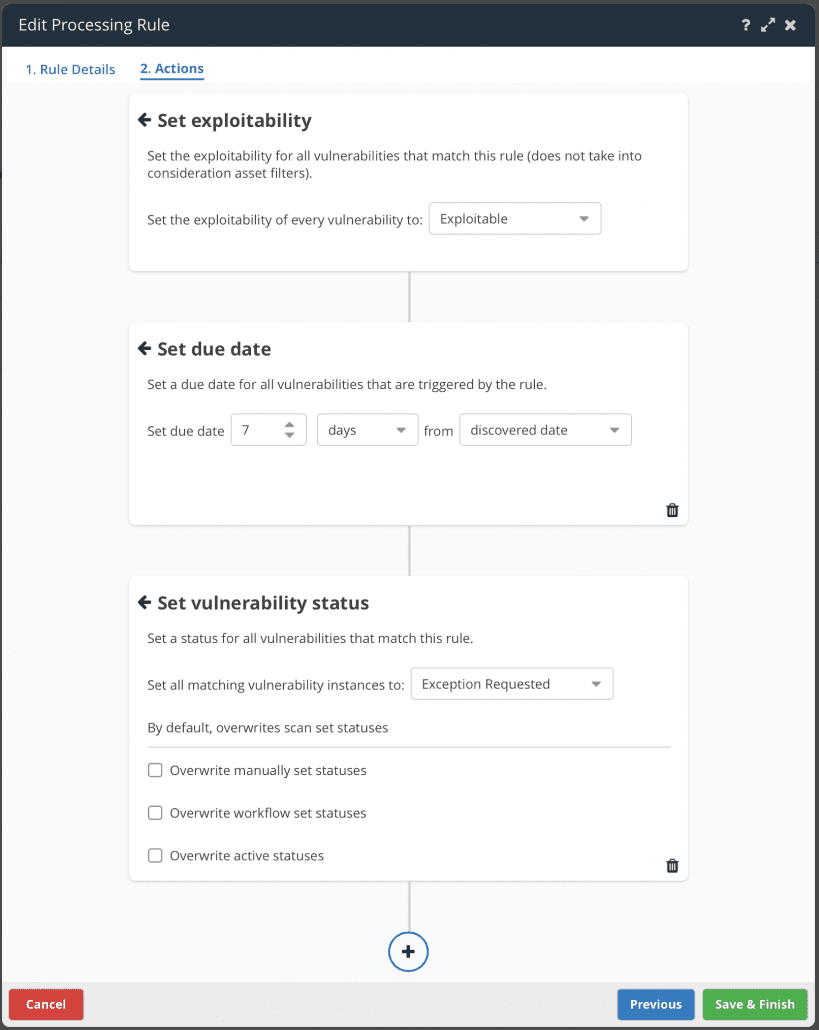
Actions in Vulnerability Processing Rules
Last release we announced Vulnerability Processing Rules, a new feature in the Nucleus Automation Engine that makes it easy and efficient to set due dates on vulnerabilities in line with the security policies in your organization. At the time, we promised more functionality coming soon to help you automate as much of the vulnerability analysis and tracking process as possible.
Today we’re excited to announce an extension to these rules using our new “ninja-approved” Action Card view. Now, in vulnerability processing rules you can not only trigger actions on more flexible data criteria, but you can also choose between a wider set of actions to perform on vulnerabilities when they are ingested into Nucleus. All actions can be filtered to only apply to subsets of assets for maximum flexibility and scalability in your automation ruleset.
Some of the new actions available include:
- Setting the due date of a vulnerability
- Assigning a vulnerability to a user
- Changing a vulnerability instance status (e.g. if you want to always mark a vulnerability as False Positive or Risk Accepted under certain circumstances, such as all low severity vulnerabilities on non-prod systems)
- Setting a different severity on a vulnerability with a spot to populate the reasoning why the vulnerability severity was altered (for those pesky audits)
- Commenting on a vulnerability
- Setting whether or not the vulnerability is exploitable (you want to automatically mark a vulnerability as exploitable when Recorded Future score is above a 90? We got you.)
But wait…
What’s even more exciting is that you can do all of the above actions in one rule. Simply create a new rule, choose the vulnerability and asset criteria, and add action cards to your heart’s content! We think that this can be particularly useful for actions that are specific to your organization, such as changing the vulnerability’s severity, assigning it to a user and adding an explainer comment all in one go, completely automatically as new vulnerability data comes into Nucleus.
Dynamic Fields/Templating Language
This was the “Eureka” moment that allowed the Nucleus Ninja to come to the simple following conclusion
“If I could just use asset fields dynamically in automation rules, I could have one rule to… rule them all!”
Well, it’s time to get back to your computer and fire up your browser, because Nucleus has got you covered! Introducing Dynamic Fields, a templating language for the Nucleus Automation Engine (and soon to be app-wide, or world-wide, depending on how you look at it).
Dynamic Fields allow you to construct asset and/or vulnerability processing rules that dynamically include information from the assets that the automation rules match during execution of the rule. For example, let’s say you want to automatically assign a vulnerability to a user based on the asset owner. That is now totally possible! Say goodbye to multiple rules for every possible value of a custom metadata field. You can create ONE rule to undertake multiple actions and dynamic values based on other attributes from elsewhere in Nucleus.
In this release, you can use asset fields dynamically in vulnerability processing rules when commenting on a vulnerability or assigning the vulnerability to a user, and in asset processing rules when adding an asset to an asset group or setting the asset owner.
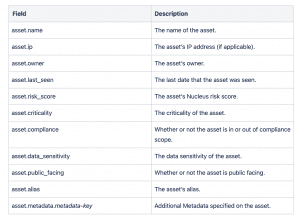
Here is a complete list of the asset fields that you can use dynamically in these automation rules:
More Additional Metadata!
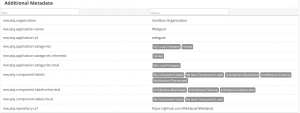
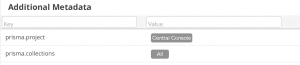
We didn’t stop there! Since you can use custom metadata from your extended asset record in Nucleus, we’re now always continuing to update existing connectors to include more additional metadata so you can use the data for better automation and reporting. In this release we’ve made updates to the Sonatype NexusIQ and Prisma Cloud connectors:
Sonatype NexusIQ
Prisma Cloud
As always, you can use all of the above metadata in the Nucleus Automation Engine to make more and more powerful automations in your Nucleus Projects.
Complete list of changes and bug fixes…
- NEW The latest CSV export AlertLogic scan output is now supported by Nucleus the in which three field names changed.
- NEW You can now use asset fields dynamically in automation rules.
- NEW Vulnerability processing rules now support multiple actions in one rule.
- NEW Asset processing rules now support setting the asset owner.
- UPDATE We’ve adopted a standard naming convention for tickets and issues in Nucleus. We now refer to all external issues as Tickets across Nucleus.
- UPDATE You can now trigger automation rules using the vulnerability source tool.
- UPDATE Updated the Welcome to Nucleus email to direct to the new Help Center.
- UPDATE Sped up the initial load of the vulnerability trends page.
- UPDATE The Sonatype NexusIQ connector now ingests additional metadata for assets.
- UPDATE The Prisma Cloud connector now ingests additional metadata for assets.
- UPDATE The SonarCloud and SonarQube connectors have been updated to not need administrator permissions in certain situations.
- UPDATE Operating System information ingested from Microsoft Defender for Endpoint now takes precedence over the same information that has been ingested from unauthenticated Tenable scans.
- UPDATE The report scheduler has been updated based on user feedback to make it easier to edit previously scheduled reports.
- UPDATE Added software export information to the Assessments module report
- BUG FIX Scan dates in some locations in the UI were not being correctly adjusted to reflect local timezones.
- BUG FIX Veracode was not importing the latest scan in certain circumstances
- BUG FIX Zendesk was not pulling ticket status back to Nucleus in certain situations.
See Nucleus in Action
Discover how unified, risk-based automation can transform your vulnerability management.































